Joseph Herrin (06-24-2013)

Matthew 10:16-17
“Behold, I send you out as sheep in the midst of wolves; therefore be wise as serpents, and innocent as doves. But beware of men…”
This blog post contains practical information promoting an awareness of the world we live in and how to walk wisely in the midst of it. There are some who would suggest that Christians need not be concerned about issues such as privacy and government spying on the populace. I disagree. Yahshua instructed His disciples to “beware of men.” We are admonished to be “wise as serpents.” Neither ignorance nor naivete are extolled as Christian virtues in the Bible. Tragically, I have found that Christians are some of the least informed, most gullible, and easily deceived members of the human race.
Perhaps some of the problem lies with a misperception of Scripture passages such as the following:
I Corinthians 14:20
Brethren, do not be children in your thinking; yet in evil be babes, but in your thinking be mature.
The apostle Paul is NOT advocating that we be ignorant of the fact that there are evil men with evil intentions all around us. Rather, he is counseling the saints to be pure in their thoughts, not pursuing a course of evil. We are to walk blamelessly ourselves, while being aware of the evil and dangers around us. The apostle elsewhere states:
Ephesians 5:15-17
Therefore be careful how you walk, not as unwise men, but as wise, making the most of your time, because the days are evil. So then do not be foolish…
There has been much in the news of late about government programs of the U.S. and other nations, that engage in spying on the communications of foreigners and their own citizens. Despite all the press, the half has not been told. In the area of government intrusion into the private affairs of citizens, I am persuaded that the majority of Christians do not have an inkling about the true extent to which their lives are monitored. This is an important subject in which to be informed that the saints might walk wisely in a world that is quickly falling into a condition of totalitarian government oversight and persecution of any who march to the beat of a different drummer.
My professional background, prior to being called to a full-time ministry of writing and teaching, provided me with some insight into the capabilities of electronic spying. I was employed at a hospital complex in the field of Microcomputer Management. In this position I was tasked with the oversight of hundreds of computers, printers, and various peripheral devices. I was responsible for maintaining them in working order, and this required some knowledge of both computer hardware and software.
When I first began in this field, most of the personal computers I oversaw were standalone devices. They were not networked, and the Internet was in its infancy. Over time I saw the evolution of the use of personal computers from standalone to networked devices. This brought with it concerns for data security, especially in a healthcare environment where patient information needed to be kept confidential. Yet, the networking together of computers also opened up opportunities for greater ease of management of end-user’s computer systems.
Back when we were using Windows 95, Windows 98 and Windows ME (Millenium Edition) on most of our personal computers, I researched and became familiar with remote administration software that would allow me to sit at my desk in my office and connect to another user’s computer. From my office, I was able to see exactly what they were viewing on their screen. I could take control of their mouse and keyboard remotely. I could pull up a directory of the files on the user’s computer, and view it right next to a directory of files on my computer. If I needed to copy a file from my computer to another user’s system, or from their computer to my own, it was as simple as dragging and dropping the file from one computer to another.
These capabilities were not built into the Windows Operating system at the time, so we had to purchase a third party product. The software could be installed by visiting the individual’s workplace, or installed across the network without needing to personally visit the user’s location. There was a parameter that could be set to cause the remote access software to either pop-up a small message box to indicate when it was running on a user’s desktop, or to be invisible to the end user. Although the purpose of the software was to aid in the administration of the hundreds of computers I was tasked with maintaining, it could be used to spy on an individual, and to observe everything they were doing. These capabilities were available through third party software vendors nearly twenty years ago.
Beginning with Windows XP, which was released by Microsoft in August of 2001, it was no longer necessary to purchase a third party product to have the capability to access a computer remotely, or to take control of its mouse and keyboard. Microsoft included a feature called Remote Assistance in the operating system itself.
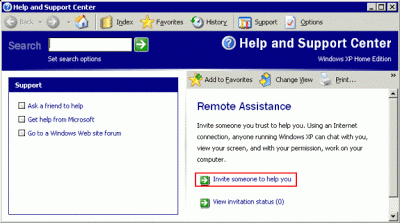
You can read about this Microsoft Administration Tool at the following link:
Windows Remote Assistance
http://windows.microsoft.com/en-us/windows7/what-is-windows-remote-assistance
This capability to access and take control of a computer has been included in every Windows operating system since XP up through the present release of Windows 8. Nevertheless, the majority of users are unaware of this feature on their computer.
I would interject here something I believe to be true. Every major world corporation, including technology companies such as Microsoft, Apple, Google, Cisco Systems, and Facebook, are permitted to attain their position of ascendancy, and to maintain their viability, only by collusion with the corporate masters of the New World Order. You will find that these corporations were only able to succeed as they received infusions of money from major banks, support from the Illuminati controlled media, and the acquiescence of governments under the dominion of the same rulers. It follows quite logically that these corporations are following an agenda dictated by their global masters. Many of the capabilities of the hardware and software systems that are sold by these major technology companies are there to serve the agenda of the hidden hand that guides them.
If you think this sounds like some far-fetched conspiracy theory, I encourage you to read the series I posted last year titled Dragon Flood. The world is a much darker and deceptive place than most people (including Christians) realize.
http://www.heart4god.ws/H4G%20Website_htm_files/Dragon%20Flood.pdf
I have no doubt that the government of the United States has contributed to the development of the Windows operating system, as well as other popular alternatives. They have guided the development of both hardware and software to insure that they are provided a back door to spy on the citizens of the world whether in their homes, at their places of employment, or in the realm of academia. Such conclusions are not speculative, for the government has passed laws requiring that technology companies assist them in this way.
The Electronic Frontiers Foundation, a watchdog and lobbying organization focused on Internet freedom, has an article posted on a government program referred to as CALEA which was being greatly expanded to require that manufacturers of computer hardware and software make it easier for the government to tap into, and monitor, all computer traffic. Following is an excerpt from the article.
The Perils of Wiretapping the Internet
EFF and a coalition of public interest industry and academic groups filed suit in 2005 challenging the Federal Communications Commission’s (FCC) unjustified expansion of the Communications Assistance for Law Enforcement Act (CALEA). By forcing broadband Internet and interconnected voice over Internet Protocol (VoIP) services to become wiretap-friendly the FCC ignored CALEA’s plain language and threatened privacy security and innovation.
Congress passed the Communications Assistance for Law Enforcement Act (CALEA) in 1994 to make it easier for law enforcement to wiretap digital telephone networks. CALEA forced telephone companies to redesign their network architectures to make wiretapping easier. It expressly did not regulate data traveling over the Internet.
But now federal law enforcement agencies want to change that. On March 10 2004 the Department of Justice (DOJ) the Federal Bureau of Investigation (FBI) and the Drug Enforcement Administration (DEA) filed a joint petition with the FCC. The petition requested that CALEA’s reach be expanded to cover communications that travel over the Internet. Thus Broadband providers would be required to rebuild their networks to make it easier for law enforcement to tap Internet “phone calls” that use VOIP applications such as Vonage as well as online “conversations” using various kinds of instant messaging (IM) programs like AOL Instant Messenger (AIM).
[Source: https://www.eff.org/issues/calea]
Please note that this expansion of CALEA was accomplished in 2004, nearly a decade ago. Nevertheless, the news focused around the revelations of whistleblower Edward Snowden has struck the world like a bombshell when he has disclosed nothing more than the fact that the American government through agencies such as the NSA has been making use of the wiretapping capability that Congress required technology companies to build into their systems. Why should this be startling news?
That this information is being touted widely now by the mainstream media, as the Edward Snowden case is receiving major public air time, is itself a subtle form of deception. Articles have been posted criticizing government officials who have lied and given perjured testimony to Congress about what their capabilities are, and what they are doing with the data. Some government officials have said they are collecting NO INFORMATION on American citizens. Later they amended this to declare that they are collecting only metadata such as phone numbers called, time of the call, and length of call, while denying that they were monitoring and storing the content of calls. Similar claims were made regarding Internet communications. Now it is being admitted by some that the government is indeed intercepting and storing the contents of phone calls and Internet communications, while it is being claimed that the information can only be accessed by order of a judge. This too is proving to be a lie, as Edward Snowden’s testimony is revealing.
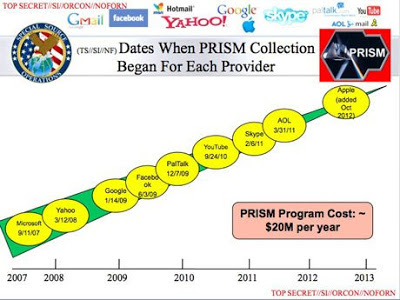
Slide Made Public by Edward Snowden

Slide Made Public By Edward Snowden
As these slides reveal, the government is collecting e-mail, chat sessions, videos, photos, stored data (such as DropBox), voice communications (such as Skype), file transfers, and every other type of communication that passes over the world’s internet and telephony networks. The focus on requests for information from vendors such as Google and Facebook is itself a form of disinformation. The limited number of formal government requests for user data from these companies provides the illusion that the government is gathering only limited content on users. The truth of the matter is that the government is tapping into the internet at the hubs and switches that form the backbone for ALL communication. They are capturing ALL Internet traffic, and storing it for retrieval whenever necessary.
Some of the types of information the government is compiling into huge data depositories will surprise many individuals. You do not even have to be transmitting data for the government to collect it. The government can spy on users proactively by activating the microphone in their cell phone, or turning on the video camera on their cell phone, laptop computer, or tablet computer, without the user knowing it is being done.
Twenty years ago when I was managing computers over an internal company network, we had the capacity to turn on a computer remotely when it was shut off. The network cards we purchased had a feature built into them called Wake On Lan (Lan is an abbreviation for Local area network). I could sit in my office and send a signal to a powered off computer in another building and power it on. I could then log onto the computer, accessing it as if I were sitting in front of the keyboard. Such capabilities have only improved over the passing years.
Fox news reported some months ago on the FBI’s ability to listen in on people’s cell phones even when the individual was not making a phone call. The person could be sitting in a restaurant, chatting with the person across from them, and the FBI could listen to every word, record it, store it, and bring it up for retrieval at will.
It may shock you as well to know that the government has the capability to turn on the video camera on your computer, or smart phone, whenever they wish. There was some outcry months back when it was discovered that a public school system that gave every high school student a laptop computer was activating the cameras in them to spy on the students. One student was shocked when his camera came on when he was in his bedroom. He could have been undressed while some individual was remotely capturing video. When the student sued the school system it was disclosed that the camera on his computer was activated more than 400 times in a two week period, often late at night when he was at home.
http://www.huffingtonpost.com/2010/10/11/lower-merion-school-distr_n_758882.html
Numerous media articles on this topic state that the user can be warned that they are being viewed remotely if the activity light on their camera comes on unexpectedly. However, many computers and smart phones do not have activity lights. Also, the activation of a light is controlled by software. It is not beyond the capacity of a spy agency with an annual budget of billions of dollars to interfere with the normal function of a camera’s activity light, allowing a video camera to record without the light coming on.
Following is a YouTube video where a user reveals how his visit to an Internet website activated his computer’s web camera without his permission.
Adobe Flash Turn on Webcam of People Visiting Website
http://youtu.be/-LbvglVj8Ho
The example above is a rather primitive example of how a web camera can be activated while visiting a website. There are far more sophisticated ways of doing so. I personally would recommend that anyone with a laptop computer with a built in video camera treat it as if it is on and recording them at all times. The same is true for smartphones, tablet computers, or desktop systems that have cameras attached to them. Not only is there a high probability that the government is recording individuals routinely through such devices, but they are storing the information away permanently to be pulled up as the opportunity, or need warrants.
Perhaps there is a pastor somewhere who has been speaking out against some evil in society and the government wishes to silence him. This same pastor may have at times viewed pornography on his computer. This information could be used to coerce the minister into silence, or agreement with some immoral government agenda. Even as the government has developed sophisticated software to listen in on telephone conversations, and to flag any communication where certain key words are spoken, so too can they develop software to turn on the video camera, or to initiate screen captures on a person’s computer, whenever they visit a pornography site.
Sound far fetched? Not at all. There are software programs that you and I can purchase today that will accomplish basically the same thing. Following is an ad for a computer security package that can respond in various ways when particular websites are accessed, or key words are typed in. This program can also be monitored remotely.
Why would the government NOT employ the same capabilities? The U.S. government is spending billions each year for Cyber Warfare. It would be naive to believe that this warfare is aimed only at foreign nationals. The same government agencies that developed the highly sophisticated Stuxnet virus that destroyed hundreds of nuclear centrifuges in Iran is capable of developing stealthy and elegant software tools to spy on American users. An article online reported on a Chinese government website that was spreading a variant of the Hupigon Backdoor virus. The computer security website F-Secure reported that this professionally developed malware, once installed on a computer that visited the site, would provide the following capabilities.
• It allows others to access the computer
• Allows for recording with the user’s webcam
• Can make the user’s computer to attack various servers
• Send victim’s computer messages
• Has rootkit functionality so it has a stealth component that hides files
• Create logs from keystrokes, steals passwords, and sends this information to remote servers
A government that has passed legislation requiring that hardware and software manufacturers make their products accessible to spying surely intends to exploit these capabilities. Edward Snowden provided an explanation for one possible government motive. When asked why people should care about surveillance, Snowden responded:
Because even if you’re not doing anything wrong you’re being watched and recorded. And the storage capability of these systems increases every year consistently by orders of magnitude to where it’s getting to the point where you don’t have to have done anything wrong. You simply have to eventually fall under suspicion from somebody even by a wrong call. And then they can use this system to go back in time and scrutinize every decision you’ve ever made, every friend you’ve ever discussed something with. And attack you on that basis to derive suspicion from an innocent life and paint anyone in the context of a wrongdoer.
[Source: http://www.policymic.com/articles/47355/edward-snowden-interview-transcript-full-text-read-the-guardian-s-entire-interview-with-the-man-who-leaked-prism]
To put this into a Biblical framework, the book of Revelation describes Satan as “the accuser of the brethren.”
Revelation 12:10-11
And I heard a loud voice in heaven, saying, “Now the salvation, and the power, and the kingdom of our God and the authority of His Christ have come, for the accuser of our brethren has been thrown down, who accuses them before our God day and night.”
Satan has many agents working for him in this hour to establish a New World Order. These human agents employ the same tactics as the fallen angel they serve. They accuse that they might condemn. To facilitate this work they are storing up massive amounts of data, audio, video, and written evidence to be used against their enemies.
To the Christian out there who has viewed pornography on the computer, there is a very good possibility that this information is filed away, along with screen shots of the images you viewed, and possibly even video capture taken from the webcam of your computer showing you looking at this material. You may have repented of such actions, and Yahweh forgiven you, exercising mercy, but Satan will show no mercy, nor will his disciples.
This should cause any Christian to walk carefully, fearing lest they give the adversary ammunition to be used against them. Your computer camera and microphone can record everything that transpires within their range. If you keep a computer in view of a bedroom, or bathroom, or other area that you have considered private, you have rendered that place a public forum. Everything in view of the camera and hearing of the microphone can be recorded.
The government, and various technology companies in league with them, are working continuously to expand this coverage and to remove all privacy. Both Google Glass and the Microsoft Xbox One represent profound leaps forward in the government’s ability to monitor the lives of people everywhere.

Google Glass (Little Sister is Watching You)
There is an article at the following link that describes some of the privacy issues raised by Google Glass.
http://www.policymic.com/articles/29585/3-new-ways-google-glass-invades-your-privacy
Google and Microsoft are leading companies in the employ of the Illuminati. Bill Gates, the billionaire co-founder of Microsoft, is a cheerleader for everything that the New World Order is pressing toward. He has given millions of dollars to Planned Parenthood, and is focused on issues related to decreasing the population of the earth. His company is a tool of the NWO. The new Xbox One entertainment and gaming console is designed to provide the government with an advanced portal into people’s homes. The Xbox One uses the Kinect motion sensing system that has had recent upgrades to allow it to determine the number of people in a room, and to even monitor a person’s heartrate. Following are some comments on this technology.
The patent, submitted on April 26, 2011, and passed on Nov. 1, 2012, essentially allows the company to remotely turn on any cameras, be they mobile or from something like the XBox Kinect, and count the number of ‘consumers’ watching licensed content.
[Source: http://www.businessinsider.com/microsoft-patent-uses-kinect-and-mobile-cameras-to-count-people-in-your-living-room-2012-11]
The terrifying thing about this patent is that it would grant copyright holders virtual access to private dwellings. The patent application suggests that the technology could be applied to head-mounted devices, large screens, computers and even mobile phones.
[Source: http://www.vg247.com/2013/05/24/microsofts-kinect-patent-suggest-they-will-be-always-be-watching/]
Microsoft ran into a storm of criticism when they announced that the new Xbox One would have to be connected to the Internet in order to play games, and would have to be connected at least once every day.
The company revealed that its upcoming Xbox One gaming console will be “always on,” a startling feature in the wake of revelations about the National Security Agency’s efforts to collect American citizens’ phone and e-mail records. The Xbox One system will require an online connection to allow users to play games they have purchased themselves (the system requires a login to Xbox Live at least once every 24 hours)…
There’s more. In addition to the required online tracking system, Xbox One will ship with the second generation of Microsoft’s Kinect motion sensor in the box, a connection to which will be required for players to use their consoles. The Kinect 2 is also “always on.” It’s able to identify individuals based on face and body recognition, works in the dark, records audio and is constantly connected to the Internet and 300,000 Microsoft servers. Even when your Xbox One is off, the Kinect is still listening, watching and waiting. (It’s also worth noting that late last year Microsoft filed for a patent that would use the Kinect camera to monitor the number of viewers in a room, checking to see if the number of people in a given room exceeded a particular threshold set by the content provider. Too many occupants, and the user would be prompted to purchase a license for more viewers.)
As a series of bullet points, it’s rather grim stuff – a new and seemingly more menacing level of Big Brother oversight.
[Source: http://www.rollingstone.com/culture/news/xbox-one-features-create-privacy-concerns-20130613]
It is not difficult to read into these requirements some nefarious government motives. This is the ultimate monitoring device. It can listen. It can see (even in the dark). It can count the number of people in a room. It can even identify people individually. That the government would want such a device to remain on at all times is consistent with their goal to know what every person is doing and thinking at all times.
When a storm of protest threatened to abort the acceptance of this new gaming system, Microsoft backed down from some of their stated requirements for this system’s operation. After all, it will not fulfill the desires of its designers if no one buys, or uses it. Nevertheless, I anticipate that Microsoft will return to its previous requirement of a constant Internet connection, and a connection at least once every 24 hours, after the system has been widely adopted. This will permit the government to gain access daily to individual’s lives. It may be possible for it to record data when offline, and then to transmit it each day when it is required to be connected.
With the current emphasis upon cloud computing, more people are keeping their personal data on the Internet where it is accessible to those who control the infrastructure. At the same time, major web presences are getting more sophisticated in tracking what users are doing, and even predicting what you may do in the future. I am not surprised anymore when I search on a product through Google and then find that in the following hours and days I am accosted by advertisements related to the specific search. I experience the same thing through Amazon’s website.
These websites are getting more sophisticated at analyzing people’s Internet viewing habits and predicting what they may want in the future. At times I have found this very helpful. Yet, at the same time it reveals the need for caution. Everything a person does on the Internet is recorded. Some of those doing the monitoring do not have my best interests, or yours, in mind.

Walk wisely, and be innocent of evil. Big Brother is watching you.
Additional Resources:
Spy Software Used By Merion School System
http://youtu.be/hHu92imqJec
Cover Your Webcam
http://youtu.be/dpoFXx-gQds
GPS Tracking Via Cellphone
http://www.wikihow.com/GPS-Track-a-Cell-Phone
Garmin NUVI Spy Matrix
http://car-gps-navigation-systems-news-zoneo.blogspot.com/
NSA Spying
http://news.cnet.com/8301-13578_3-57589495-38/nsa-spying-flap-extends-to-contents-of-u.s-phone-calls/
Heart4God Website: http://www.heart4god.ws
Parables Blog: www.parablesblog.blogspot.com
Mailing Address:
Joseph Herrin
P.O. Box 804
Montezuma, GA 31063


Thank you for posting this. I knew it was getting bad, but I didn't know how bad. I believe everything you have here, I have experienced strange happenings with my computer lately. There are times when I've logged out and went off to other things or even to bed, and when I come back, I am no longer logged out, and it show's me the last screen I visited such as email or face book or my blog. I have talked to others who say the same thing. This is something that has never happened before until just recently. I don't know what can be done, but it's good to know what's going on. It's time for those silent and asleep to wake up. God Bless and keep you.
People who think they have nothing to worry about the government spying because they don't do anything bad, need to think again. If they wanted to silence a critic or frame someone for terrorist activity, they could take control of that person's mouse and remotely visit any incriminating or illegal site they want to leave "evidence" to be found on that person's computer.
Even send fake emails from that persons computer "confessing" to a friend. This "evidence" is often enough to convict in a court of law! If information = power, and absolute power corrupts absolutely, then what do you get with absolute information?
Jennifer,
That's exactly what I was thinking when I read of Christians visiting porn sites. Couldn't we be framed through remote access with such offenses?
In fact, as soon as it becomes illegal to utter "fundamentalistic" statements such as "JESUS is the only way to be saved" and Christianity is equated to terrorism (coming soon, as Joseph's blogs make it clear!), a lot of us are going to be persecuted…
I've been pondering this issue and thought, oh well, I'm probably in some black list already, so be it! I'll keep preaching and teaching as long as I have a voice here on the Web. God will honor people who refuse to deny Him in spite of increasing intimidation and threats.