Joseph Herrin (10-30-2013)
The Bible teaches that one of the defining characteristics of the last days will be lawlessness. I believe it would be profitable to identify what this lawlessness will look like. Some may have the mistaken idea that the last days will be a time when there is no strong central government, leaving the people of the nations to rampage unimpeded in a wild display of global anarchy.
Although I foresee plenty of civil unrest arising in the coming days, it will be met with the overwhelming force of a highly militarized government. Dissent will be crushed as Satan moves to erect his New World Order out of the ashes of the old nationalistic system of governments. There will be tremendous conflagrations as patriots resist that which is to come. Millions will die. Others will be imprisoned as the cruel hand of global tyranny asserts itself.
Revelation 13:10
Anyone who is destined for prison will be taken to prison.
Anyone destined to die by the sword will die by the sword.
NLT
When the New World Order has been established, the Beast government will be known for its rigid control of the masses. A surveillance society similar to that in the novel 1984 will be in place. What people whisper in their bedrooms will be heard by the men wielding the truncheons of the beast system. Already we are seeing that the pieces are being put in place for government to spy on every activity of humanity. It has been disclosed that the government can activate the microphone on nearly any cell phone and listen in to all that is happening, even when no phone call is being placed. It is known that the government can activate the video camera and microphone on people’s computers, and record whatever is visible or heard.
Computer chip manufacturer Intel recently announced that their new computer chips have 3G wireless access built into them. This gives the government the ability to tap into anyone’s computer system, even if it is turned off, and to access all your personal correspondence, files, passwords, etc..
Yesterday I was reading online and someone was discussing dumping Windows because Microsoft has given the government backdoor access to the operating system. The person said they were switching to Ubuntu, a variety of the Linux operating system. If they have one of these new Intel chips, switching to another operating system will not do them any good. The video clearly states that this access feature is independent of the operating system. In fact, you do not even need to have an operating system installed, for access to the computer is gained at the chip level on the computer’s motherboard. Your computer can even be turned off and it can be remotely switched on.
We are seeing such capabilities sold to the public as advanced security features in the same way that governments are forever promoting the need to keep nations and peoples safe by monitoring them more and more. What these features actually do is remove all privacy from the individual. Every action, every word, is monitored, searched, and screened to check for anything that might be a threat to the arising beast system.
As I sit here in my 41 year old school bus in a campground on Jekyll Island, I am aware of numerous ways that my privacy is being invaded. I have a TomTom GPS on my dash for navigation. Approximately every week or two it turns itself on all by itself, and has been doing so for a couple years. By simply powering up it can report my exact location back to anyone monitoring the signal. I have noticed that my Verizon cellphone, which is a simple feature phone, and not even a smartphone, activates every night at 4:15 A.M.. I keep the phone by my bed to use as a clock when I want to check the time. I have noticed that its lights brighten as if it is being accessed every night at this same time. The GPS feature in it can also report my location. Aside from this, the camera and microphone can be accessed remotely at any time by the FBI, NSA, or any number of other government agencies who engage in spying.
My laptop computer that I use for all of my ministry work runs on an Intel i7 processor and has Windows 7 operating system. Both the processor and the operating system provide entry points for the government to gain access to all of my files, or to activate the camera or microphone and listen in. If you use Skype, Microsoft purchased this popular communication program last year and promptly redesigned it to give the government access to every Skype session. It should be noted as well that by gaining chip level access to an individual’s computer, installing an encryption program will not shield your private data from prying eyes. The computer processor is able to utilize key-logging techniques to record every button that is pressed on a keyboard, so even if the data is encrypted before it is stored on a hard drive or transmitted across the Internet, it has likely already been read and stored by the key-logging software.
I also have a Kindle Fire tablet. Amazon is announcing a new feature called the “Mayday button” on their most recent Kindles that allow a service tech to remotely access the tablet, take control of it, and even draw on the screen while they are speaking to you. If they have this level of access, then you can be certain that the government does as well.
It should not be overlooked that this remote access to a computer or tablet also gives another party the ability to load software, install files, and to create a false history of computer usage on a person’s computer. It would be very easy to frame an innocent person by installing child pornography, or altering files to make it appear that the person was researching terrorism related topics.
In addition to this, 96% of new cars have black boxes built into them that can allow them to be tracked, and remotely accessed. Published data states that the black boxes record data ONLY a few seconds before or after an accident. How do they know to record data before an accident? The answer is they don’t, so they record data continuously. Knowing that the government has had agreements with computer hardware and software manufacturers for years to give them back door access to anyone’s computer, it is quite reasonable that they also have installed remote monitoring of this automotive data. A similar technology as the Intel 3G system would not be difficult to implement. The government owns General Motors and GM installs black boxes in 100% of their vehicles.
If your car has Onstar, or a similar dashboard computer system, the government has been listening in on your conversations in your vehicle for years. A lawsuit was brought back in 2003, a full decade ago, to block the government from doing so. That just means that since 2003 the government has not been able to publicly admit they are listening in on people’s conversations as they drive their cars down the road.
http://news.cnet.com/Court-to-FBI-No-spying-on-in-car-computers/2100-1029_3-5109435.html
One troubling development is that the governments of several states are now talking about taxing people according to the number of miles they drive in their cars. Until now, highway taxes have been collected at the pump, and there is no good reason that taxes should not continue to be collected in this manner (electric cars are still a minuscule percentage of vehicles traveling the roads). However, under the guise of taxing people more fairly, the government will gain the ability to track every individual’s location.
http://www.latimes.com/nation/la-na-roads-black-boxes-20131027,0,6090226.story
The electric smart meter on your house also reports data back to the government, and a burgeoning number of home appliances are reporting information and being used as behavior tracking devices.
http://rt.com/news/cia-spy-people-petraeus-795/
In addition to this, the government is installing millions of cameras and microphones throughout cities and along highways to track people.
With all of this surveillance, one might ask how anyone would get away with being “lawless” in the coming New World Order? The government is seeking to eradicate anonymity. They want to know what everyone is doing and saying all the time. If this is to be the state of the New World Order, the Beast system that the Bible foretells, how could citizens possibly get away with lawlessness? To answer the question, we must understand what the Bible means by lawlessness. Let us begin by reading the following passage of Scripture.
II Thessalonians 2:1-10
Now we request you, brethren, with regard to the coming of our Lord Yahshua Christ, and our gathering together to Him, that you may not be quickly shaken from your composure or be disturbed either by a spirit or a message or a letter as if from us, to the effect that the day of the Lord has come. Let no one in any way deceive you, for it will not come unless the apostasy comes first, and the man of lawlessness is revealed, the son of destruction, who opposes and exalts himself above every so-called god or object of worship, so that he takes his seat in the temple of God, displaying himself as being God. Do you not remember that while I was still with you, I was telling you these things? And you know what restrains him now, so that in his time he may be revealed. For the mystery of lawlessness is already at work; only he who now restrains will do so until he is taken out of the way. And then that lawless one will be revealed whom the Lord will slay with the breath of His mouth and bring to an end by the appearance of His coming; that is, the one whose coming is in accord with the activity of Satan, with all power and signs and false wonders, and with all the deception of wickedness for those who perish, because they did not receive the love of the truth so as to be saved.
When the Bible speaks of the last days being a time of great “lawlessness” it is not speaking about violating man’s laws. It is speaking of violating God’s law. I am not here speaking of the Law of Moses, but rather of the much broader sense of God’s righteousness and holiness, His will for all men in all situations. This is what men and women and children will be violating.
Throughout the ages of this present creation Yahweh has restrained the sinfulness of man. When man’s every thought and action became wickedness in the time of Noah, Yahweh brought judgment upon man, and began over with 8 individuals. After the flood Yahweh also greatly shortened man’s lifespan so that he would not become so thoroughly corrupted by evil. This shortened lifespan has had an immense impact upon limiting the wickedness of mankind.
We also see Yahweh judging cities and peoples who gave themselves fully over to the pursuit of wickedness. He rained fire and brimstone upon Sodom and Gomorrah in the days of Abraham. Nearly 1,500 years later, He did the same thing when Pompeii, Herculaneum, and other nearby cities were destroyed in the eruption of Mount Vesuvius in 79 A.D.. Yahweh has continually cast down peoples and nations that became exceedingly wicked, yet we read that in these last days, “he who now restrains will do so until he is taken out of the way.” Then we will see the evil of men in its full vileness. These will truly be lawless days. The Beast government will rule the world, and will make every form of evil acceptable. We are seeing this occurring globally now as nation after nation is normalizing homosexual behavior, a behavior that Yahweh characterizes as an “abomination.”
I have mentioned a few times that pedophilia, the sexual exploitation of children, is one of the next areas of sin to be normalized. Homosexuals are renowned for their attraction to children. Observe how many Roman Catholic priests were having sexual relations with young boys. The same is true of Jerry Sandusky at Penn State. It is also true of Harvey Milk, the first openly homosexual man to be elected to any public office in America. The U.S. Postal Service recently announced they will be issuing a stamp to commemorate the life of Harvey Milk. A biography of Harvey Milk reveals that he was a sexual predator who preyed on young boys.
http://godfatherpolitics.com/13047/obama-honors-sexual-predator-harvey-milk-postage-stamp/
People of God, this is an example of lawlessness. In 2009 President Barack Obama posthumously awarded Harvey Milk the Presidential Medal of Freedom. Harvey Milk’s life ambition was to liberate people from Yahweh’s definition of sexual morality. The only freedom he brought was bondage to sin and slavery to sexual deviance. Yet this godless man is being set forth as a national hero, someone to be emulated. The state of California has even proposed that a Harvey Milk Day be observed each year where school children would be required to discuss some positive achievement of this godless, homosexual, child abuser.
One of the key duties of any moral nation is to protect its children from those who would abuse them sexually, physically, or mentally. Yet, America is giving her children over to be abused. Is it any surprise that a nation that has murdered tens of millions of their unborn is now moving to abuse those who have been born. A shocking story appeared this week regarding the Obama administration’s push to have Common Core adopted by the school systems of all 50 states. Already, 45 states have signed on. The Common Core program would regiment all education so that the same subjects are being taught at the same time on the same day in every government school throughout America.
The overseers of the Common Core program are not elected, and their decisions are not subject to appeal. Common Core has drawn up a list of “exemplar texts” that are to be read and discussed in each of the grades. The word “exemplar” means “a model or pattern to be copied or imitated: George Washington is the exemplar of patriotic virtue.”
One of the exemplar texts for the 11th grade, which consists of students who are typically 16-17 years of age, is The Bluest Eye by author Toni Morrison. The book contains GRAPHIC descriptions of incest, rape, and pedophilia written from the perspective of the perpetrator. Morrison set out to describe the thoughts of one who commits such wickedness, without any censorship, or criticism. She said she was writing from the perspective of one who is a “co-conspirator” with the rapist. The result is a book that reads like a how-to-manual for sexual predators, and encourages youth to entertain the thought processes of one who abuses others sexually. Such an action can only lead to an inestimable number of young people acting out the deviant sexual fantasies that are put in their heads.
The following website includes excerpts from the book which is recommended for all 11th graders in America to read. It is very explicit. It is outrageous that anyone could consider this suitable, even exemplary, reading material for the nation’s 16 and 17 year olds.
http://politichicks.tv/column/warning-graphic-common-core-approved-child-pornography/
One commenter to the above article stated the following:
Robin H
First you desensitize the parents with the “Fifty Shades of Grey” novels which are also about pedophilia, and then you desensitize the kids that you want to prey on. Therefore you have a whole crop of people who now think this is somehow normal.
The book Fifty Shades of Grey has been promoted endlessly by the media who seemed determined to make it a best seller. It is now scheduled to be made into a movie. The book is quite obviously pornographic. It has been described by various media as “mommy porn” as the target audience is women. What the media has not been telling people is that the book is subtly written to disguise the fact that it is actually describing the seduction and sexual exploitation of a young girl whose behavior and mental maturity could be as young as a 12 year old.
A recent article stated that 60 million copies of this book have been sold. This is evidence of widespread lawlessness. The laws being broken are Yahweh’s. He has said:
Philippians 4:8
Finally, brethren, whatever is true, whatever is honorable, whatever is right, whatever is pure, whatever is lovely, whatever is of good repute, if there is any excellence and if anything worthy of praise, let your mind dwell on these things.
The government of America, controlled by a global elite, has become a champion of immorality, and an adversary of all that is righteous and holy. The media, controlled by the same global powers, has been complicit in the dissemination of that which is indecent, prurient, and morally decadent.
It is not coincidental that the President has honored, and continues to honor, a homosexual child abuser at the same time that the youth of the nation are being instructed by his government to read material provided by the public school system that promotes pedophilia, rape, and incest. Nor is the timing of the Fifty Shades of Grey novel and movie coincidental. There is a movement afoot that is intent on normalizing the idea of adult/child sexual intercourse in the same way that homosexuality has been promoted. Like the homosexual movement in its early days, there are organizations being formed to defend pedophilia, which is being described as “minor-attracted” individuals. One of these groups is B4UACT.ORG.
http://www.b4uact.org/
Just as the homosexuals advocated to change the definition of homosexuality in the American Psychiatric Associations manual of mental disorders, so too are those who are promoting adult/child sexual relations lobbying the APA to redefine pedophilia as a normal sexual attraction.
http://sainteliaschurch.blogspot.com/2011/08/academic-conference-seeks-to-normalize.html
This is how lawlessness becomes normalized. Brothers and sisters, do not think that pedophilia will not become normalized in the same way that homosexuality has. The moral depravity of the nation is accelerating. The end of the age is before us. All restraint is being removed. Soon we will see that it is declared legal and protected activity for an individual to pursue any wicked action that enters his/her mind. This is a fulfillment of the words of Christ.
Matthew 24:12
“And because lawlessness is increased, most people’s love will grow cold.”
Matthew 10:16-17
“Behold, I send you out as sheep in the midst of wolves; therefore be wise as serpents, and innocent as doves. But beware of men…”
This blog post contains practical information promoting an awareness of the world we live in and how to walk wisely in the midst of it. There are some who would suggest that Christians need not be concerned about issues such as privacy and government spying on the populace. I disagree. Yahshua instructed His disciples to “beware of men.” We are admonished to be “wise as serpents.” Neither ignorance nor naivete are extolled as Christian virtues in the Bible. Tragically, I have found that Christians are some of the least informed, most gullible, and easily deceived members of the human race.
Perhaps some of the problem lies with a misperception of Scripture passages such as the following:
I Corinthians 14:20
Brethren, do not be children in your thinking; yet in evil be babes, but in your thinking be mature.
The apostle Paul is NOT advocating that we be ignorant of the fact that there are evil men with evil intentions all around us. Rather, he is counseling the saints to be pure in their thoughts, not pursuing a course of evil. We are to walk blamelessly ourselves, while being aware of the evil and dangers around us. The apostle elsewhere states:
Ephesians 5:15-17
Therefore be careful how you walk, not as unwise men, but as wise, making the most of your time, because the days are evil. So then do not be foolish…
There has been much in the news of late about government programs of the U.S. and other nations, that engage in spying on the communications of foreigners and their own citizens. Despite all the press, the half has not been told. In the area of government intrusion into the private affairs of citizens, I am persuaded that the majority of Christians do not have an inkling about the true extent to which their lives are monitored. This is an important subject in which to be informed that the saints might walk wisely in a world that is quickly falling into a condition of totalitarian government oversight and persecution of any who march to the beat of a different drummer.
My professional background, prior to being called to a full-time ministry of writing and teaching, provided me with some insight into the capabilities of electronic spying. I was employed at a hospital complex in the field of Microcomputer Management. In this position I was tasked with the oversight of hundreds of computers, printers, and various peripheral devices. I was responsible for maintaining them in working order, and this required some knowledge of both computer hardware and software.
When I first began in this field, most of the personal computers I oversaw were standalone devices. They were not networked, and the Internet was in its infancy. Over time I saw the evolution of the use of personal computers from standalone to networked devices. This brought with it concerns for data security, especially in a healthcare environment where patient information needed to be kept confidential. Yet, the networking together of computers also opened up opportunities for greater ease of management of end-user’s computer systems.
Back when we were using Windows 95, Windows 98 and Windows ME (Millenium Edition) on most of our personal computers, I researched and became familiar with remote administration software that would allow me to sit at my desk in my office and connect to another user’s computer. From my office, I was able to see exactly what they were viewing on their screen. I could take control of their mouse and keyboard remotely. I could pull up a directory of the files on the user’s computer, and view it right next to a directory of files on my computer. If I needed to copy a file from my computer to another user’s system, or from their computer to my own, it was as simple as dragging and dropping the file from one computer to another.
These capabilities were not built into the Windows Operating system at the time, so we had to purchase a third party product. The software could be installed by visiting the individual’s workplace, or installed across the network without needing to personally visit the user’s location. There was a parameter that could be set to cause the remote access software to either pop-up a small message box to indicate when it was running on a user’s desktop, or to be invisible to the end user. Although the purpose of the software was to aid in the administration of the hundreds of computers I was tasked with maintaining, it could be used to spy on an individual, and to observe everything they were doing. These capabilities were available through third party software vendors nearly twenty years ago.
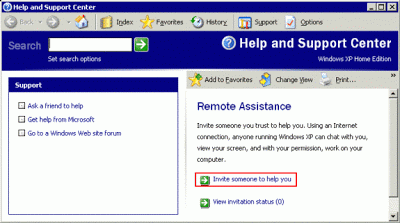
Beginning with Windows XP, which was released by Microsoft in August of 2001, it was no longer necessary to purchase a third party product to have the capability to access a computer remotely, or to take control of its mouse and keyboard. Microsoft included a feature called Remote Assistance in the operating system itself.
You can read about this Microsoft Administration Tool at the following link:
Windows Remote Assistance
http://windows.microsoft.com/en-us/windows7/what-is-windows-remote-assistance
This capability to access and take control of a computer has been included in every Windows operating system since XP up through the present release of Windows 8. Nevertheless, the majority of users are unaware of this feature on their computer.
I would interject here something I believe to be true. Every major world corporation, including technology companies such as Microsoft, Apple, Google, Cisco Systems, and Facebook, are permitted to attain their position of ascendancy, and to maintain their viability, only by collusion with the corporate masters of the New World Order. You will find that these corporations were only able to succeed as they received infusions of money from major banks, support from the Illuminati controlled media, and the acquiescence of governments under the dominion of the same rulers. It follows quite logically that these corporations are following an agenda dictated by their global masters. Many of the capabilities of the hardware and software systems that are sold by these major technology companies are there to serve the agenda of the hidden hand that guides them.
If you think this sounds like some far-fetched conspiracy theory, I encourage you to read the series I posted last year titled Dragon Flood. The world is a much darker and deceptive place than most people (including Christians) realize.
http://www.heart4god.ws/H4G%20Website_htm_files/Dragon%20Flood.pdf
I have no doubt that the government of the United States has contributed to the development of the Windows operating system, as well as other popular alternatives. They have guided the development of both hardware and software to insure that they are provided a back door to spy on the citizens of the world whether in their homes, at their places of employment, or in the realm of academia. Such conclusions are not speculative, for the government has passed laws requiring that technology companies assist them in this way.
The Electronic Frontiers Foundation, a watchdog and lobbying organization focused on Internet freedom, has an article posted on a government program referred to as CALEA which was being greatly expanded to require that manufacturers of computer hardware and software make it easier for the government to tap into, and monitor, all computer traffic. Following is an excerpt from the article.
The Perils of Wiretapping the Internet
EFF and a coalition of public interest industry and academic groups filed suit in 2005 challenging the Federal Communications Commission’s (FCC) unjustified expansion of the Communications Assistance for Law Enforcement Act (CALEA). By forcing broadband Internet and interconnected voice over Internet Protocol (VoIP) services to become wiretap-friendly the FCC ignored CALEA’s plain language and threatened privacy security and innovation.
Congress passed the Communications Assistance for Law Enforcement Act (CALEA) in 1994 to make it easier for law enforcement to wiretap digital telephone networks. CALEA forced telephone companies to redesign their network architectures to make wiretapping easier. It expressly did not regulate data traveling over the Internet.
But now federal law enforcement agencies want to change that. On March 10 2004 the Department of Justice (DOJ) the Federal Bureau of Investigation (FBI) and the Drug Enforcement Administration (DEA) filed a joint petition with the FCC. The petition requested that CALEA’s reach be expanded to cover communications that travel over the Internet. Thus Broadband providers would be required to rebuild their networks to make it easier for law enforcement to tap Internet “phone calls” that use VOIP applications such as Vonage as well as online “conversations” using various kinds of instant messaging (IM) programs like AOL Instant Messenger (AIM).
[Source: https://www.eff.org/issues/calea]
Please note that this expansion of CALEA was accomplished in 2004, nearly a decade ago. Nevertheless, the news focused around the revelations of whistleblower Edward Snowden has struck the world like a bombshell when he has disclosed nothing more than the fact that the American government through agencies such as the NSA has been making use of the wiretapping capability that Congress required technology companies to build into their systems. Why should this be startling news?
That this information is being touted widely now by the mainstream media, as the Edward Snowden case is receiving major public air time, is itself a subtle form of deception. Articles have been posted criticizing government officials who have lied and given perjured testimony to Congress about what their capabilities are, and what they are doing with the data. Some government officials have said they are collecting NO INFORMATION on American citizens. Later they amended this to declare that they are collecting only metadata such as phone numbers called, time of the call, and length of call, while denying that they were monitoring and storing the content of calls. Similar claims were made regarding Internet communications. Now it is being admitted by some that the government is indeed intercepting and storing the contents of phone calls and Internet communications, while it is being claimed that the information can only be accessed by order of a judge. This too is proving to be a lie, as Edward Snowden’s testimony is revealing.
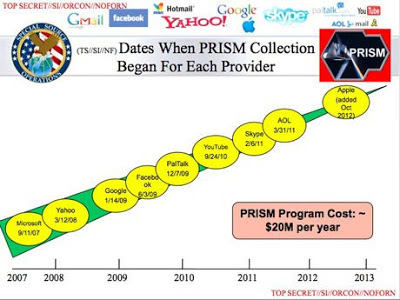
Slide Made Public by Edward Snowden
Slide Made Public By Edward Snowden
As these slides reveal, the government is collecting e-mail, chat sessions, videos, photos, stored data (such as DropBox), voice communications (such as Skype), file transfers, and every other type of communication that passes over the world’s internet and telephony networks. The focus on requests for information from vendors such as Google and Facebook is itself a form of disinformation. The limited number of formal government requests for user data from these companies provides the illusion that the government is gathering only limited content on users. The truth of the matter is that the government is tapping into the internet at the hubs and switches that form the backbone for ALL communication. They are capturing ALL Internet traffic, and storing it for retrieval whenever necessary.
Some of the types of information the government is compiling into huge data depositories will surprise many individuals. You do not even have to be transmitting data for the government to collect it. The government can spy on users proactively by activating the microphone in their cell phone, or turning on the video camera on their cell phone, laptop computer, or tablet computer, without the user knowing it is being done.
Twenty years ago when I was managing computers over an internal company network, we had the capacity to turn on a computer remotely when it was shut off. The network cards we purchased had a feature built into them called Wake On Lan (Lan is an abbreviation for Local area network). I could sit in my office and send a signal to a powered off computer in another building and power it on. I could then log onto the computer, accessing it as if I were sitting in front of the keyboard. Such capabilities have only improved over the passing years.
Fox news reported some months ago on the FBI’s ability to listen in on people’s cell phones even when the individual was not making a phone call. The person could be sitting in a restaurant, chatting with the person across from them, and the FBI could listen to every word, record it, store it, and bring it up for retrieval at will.
It may shock you as well to know that the government has the capability to turn on the video camera on your computer, or smart phone, whenever they wish. There was some outcry months back when it was discovered that a public school system that gave every high school student a laptop computer was activating the cameras in them to spy on the students. One student was shocked when his camera came on when he was in his bedroom. He could have been undressed while some individual was remotely capturing video. When the student sued the school system it was disclosed that the camera on his computer was activated more than 400 times in a two week period, often late at night when he was at home.
http://www.huffingtonpost.com/2010/10/11/lower-merion-school-distr_n_758882.html
Numerous media articles on this topic state that the user can be warned that they are being viewed remotely if the activity light on their camera comes on unexpectedly. However, many computers and smart phones do not have activity lights. Also, the activation of a light is controlled by software. It is not beyond the capacity of a spy agency with an annual budget of billions of dollars to interfere with the normal function of a camera’s activity light, allowing a video camera to record without the light coming on.
I personally would recommend that anyone with a laptop computer with a built in video camera treat it as if it is on and recording them at all times. The same is true for smartphones, tablet computers, or desktop systems that have cameras attached to them. Not only is there a high probability that the government is recording individuals routinely through such devices, but they are storing the information away permanently to be pulled up as the opportunity, or need warrants.
Perhaps there is a pastor somewhere who has been speaking out against some evil in society and the government wishes to silence him. This same pastor may have at times viewed pornography on his computer. This information could be used to coerce the minister into silence, or agreement with some immoral government agenda. Even as the government has developed sophisticated software to listen in on telephone conversations, and to flag any communication where certain key words are spoken, so too can they develop software to turn on the video camera, or to initiate screen captures on a person’s computer, whenever they visit a pornography site.
Sound far fetched? Not at all. There are software programs that you and I can purchase today that will accomplish basically the same thing.
<iframe width=”560″ height=”315″ src=”https://www.youtube.com/embed/whZGe2JLPOA” title=”YouTube video player” frameborder=”0″ allow=”accelerometer; autoplay; clipboard-write; encrypted-media; gyroscope; picture-in-picture” allowfullscreen></iframe>
Why would the government NOT employ the same capabilities? The U.S. government is spending billions each year for Cyber Warfare. It would be naive to believe that this warfare is aimed only at foreign nationals. The same government agencies that developed the highly sophisticated Stuxnet virus that destroyed hundreds of nuclear centrifuges in Iran is capable of developing stealthy and elegant software tools to spy on American users. An article online reported on a Chinese government website that was spreading a variant of the Hupigon Backdoor virus. The computer security website F-Secure reported that this professionally developed malware, once installed on a computer that visited the site, would provide the following capabilities.
• It allows others to access the computer
• Allows for recording with the user’s webcam
• Can make the user’s computer to attack various servers
• Send victim’s computer messages
• Has rootkit functionality so it has a stealth component that hides files
• Create logs from keystrokes, steals passwords, and sends this information to remote servers
A government that has passed legislation requiring that hardware and software manufacturers make their products accessible to spying surely intends to exploit these capabilities. Edward Snowden provided an explanation for one possible government motive. When asked why people should care about surveillance, Snowden responded:
Because even if you’re not doing anything wrong you’re being watched and recorded. And the storage capability of these systems increases every year consistently by orders of magnitude to where it’s getting to the point where you don’t have to have done anything wrong. You simply have to eventually fall under suspicion from somebody even by a wrong call. And then they can use this system to go back in time and scrutinize every decision you’ve ever made, every friend you’ve ever discussed something with. And attack you on that basis to derive suspicion from an innocent life and paint anyone in the context of a wrongdoer.
[Source: http://www.policymic.com/articles/47355/edward-snowden-interview-transcript-full-text-read-the-guardian-s-entire-interview-with-the-man-who-leaked-prism]
To put this into a Biblical framework, the book of Revelation describes Satan as “the accuser of the brethren.”
Revelation 12:10-11
And I heard a loud voice in heaven, saying, “Now the salvation, and the power, and the kingdom of our God and the authority of His Christ have come, for the accuser of our brethren has been thrown down, who accuses them before our God day and night.”
Satan has many agents working for him in this hour to establish a New World Order. These human agents employ the same tactics as the fallen angel they serve. They accuse that they might condemn. To facilitate this work they are storing up massive amounts of data, audio, video, and written evidence to be used against their enemies.
To the Christian out there who has viewed pornography on the computer, there is a very good possibility that this information is filed away, along with screen shots of the images you viewed, and possibly even video capture taken from the webcam of your computer showing you looking at this material. You may have repented of such actions, and Yahweh forgiven you, exercising mercy, but Satan will show no mercy, nor will his disciples.
This should cause any Christian to walk carefully, fearing lest they give the adversary ammunition to be used against them. Your computer camera and microphone can record everything that transpires within their range. If you keep a computer in view of a bedroom, or bathroom, or other area that you have considered private, you have rendered that place a public forum. Everything in view of the camera and hearing of the microphone can be recorded.
The government, and various technology companies in league with them, are working continuously to expand this coverage and to remove all privacy. Both Google Glass and the Microsoft Xbox One represent profound leaps forward in the government’s ability to monitor the lives of people everywhere.
Google Glass (Little Sister is Watching You)
There is an article at the following link that describes some of the privacy issues raised by Google Glass.
http://www.policymic.com/articles/29585/3-new-ways-google-glass-invades-your-privacy
Google and Microsoft are leading companies in the employ of the Illuminati. Bill Gates, the billionaire co-founder of Microsoft, is a cheerleader for everything that the New World Order is pressing toward. He has given millions of dollars to Planned Parenthood, and is focused on issues related to decreasing the population of the earth. His company is a tool of the NWO. The new Xbox One entertainment and gaming console is designed to provide the government with an advanced portal into people’s homes. The Xbox One uses the Kinect motion sensing system that has had recent upgrades to allow it to determine the number of people in a room, and to even monitor a person’s heartrate. Following are some comments on this technology.
The patent, submitted on April 26, 2011, and passed on Nov. 1, 2012, essentially allows the company to remotely turn on any cameras, be they mobile or from something like the XBox Kinect, and count the number of ‘consumers’ watching licensed content.
[Source: http://www.businessinsider.com/microsoft-patent-uses-kinect-and-mobile-cameras-to-count-people-in-your-living-room-2012-11]
The terrifying thing about this patent is that it would grant copyright holders virtual access to private dwellings. The patent application suggests that the technology could be applied to head-mounted devices, large screens, computers and even mobile phones.
[Source: http://www.vg247.com/2013/05/24/microsofts-kinect-patent-suggest-they-will-be-always-be-watching/]
Microsoft ran into a storm of criticism when they announced that the new Xbox One would have to be connected to the Internet in order to play games, and would have to be connected at least once every day.
The company revealed that its upcoming Xbox One gaming console will be “always on,” a startling feature in the wake of revelations about the National Security Agency’s efforts to collect American citizens’ phone and e-mail records. The Xbox One system will require an online connection to allow users to play games they have purchased themselves (the system requires a login to Xbox Live at least once every 24 hours)…
There’s more. In addition to the required online tracking system, Xbox One will ship with the second generation of Microsoft’s Kinect motion sensor in the box, a connection to which will be required for players to use their consoles. The Kinect 2 is also “always on.” It’s able to identify individuals based on face and body recognition, works in the dark, records audio and is constantly connected to the Internet and 300,000 Microsoft servers. Even when your Xbox One is off, the Kinect is still listening, watching and waiting. (It’s also worth noting that late last year Microsoft filed for a patent that would use the Kinect camera to monitor the number of viewers in a room, checking to see if the number of people in a given room exceeded a particular threshold set by the content provider. Too many occupants, and the user would be prompted to purchase a license for more viewers.)
As a series of bullet points, it’s rather grim stuff – a new and seemingly more menacing level of Big Brother oversight.
[Source: http://www.rollingstone.com/culture/news/xbox-one-features-create-privacy-concerns-20130613]
It is not difficult to read into these requirements some nefarious government motives. This is the ultimate monitoring device. It can listen. It can see (even in the dark). It can count the number of people in a room. It can even identify people individually. That the government would want such a device to remain on at all times is consistent with their goal to know what every person is doing and thinking at all times.
When a storm of protest threatened to abort the acceptance of this new gaming system, Microsoft backed down from some of their stated requirements for this system’s operation. After all, it will not fulfill the desires of its designers if no one buys, or uses it. Nevertheless, I anticipate that Microsoft will return to its previous requirement of a constant Internet connection, and a connection at least once every 24 hours, after the system has been widely adopted. This will permit the government to gain access daily to individual’s lives. It may be possible for it to record data when offline, and then to transmit it each day when it is required to be connected.
With the current emphasis upon cloud computing, more people are keeping their personal data on the Internet where it is accessible to those who control the infrastructure. At the same time, major web presences are getting more sophisticated in tracking what users are doing, and even predicting what you may do in the future. I am not surprised anymore when I search on a product through Google and then find that in the following hours and days I am accosted by advertisements related to the specific search. I experience the same thing through Amazon’s website.
These websites are getting more sophisticated at analyzing people’s Internet viewing habits and predicting what they may want in the future. At times I have found this very helpful. Yet, at the same time it reveals the need for caution. Everything a person does on the Internet is recorded. Some of those doing the monitoring do not have my best interests, or yours, in mind.
Walk wisely, and be innocent of evil. Big Brother is watching you.
Additional Resources:
GPS Tracking Via Cellphone
http://www.wikihow.com/GPS-Track-a-Cell-Phone
Garmin NUVI Spy Matrix
http://car-gps-navigation-systems-news-zoneo.blogspot.com/
NSA Spying
http://news.cnet.com/8301-13578_3-57589495-38/nsa-spying-flap-extends-to-contents-of-u.s-phone-calls/
After I posted yesterday’s blog that focused on the subject of government spying I was browsing some news sites and came across some excellent articles on the same subject. The first article I found was located on The New York Times, and was dated June 19, 2013. The information it reveals far exceeds the revelations disclosed by Edward Snowden. This really causes one to wonder what the government agenda is when it will pursue one individual for disclosing information that has been in the public domain for years, while raising no outcry about a New York Times article that shares far more egregious information.
The mainstream media has been giving the Edward Snowden story so much coverage that one has to question what the agenda is of the powers that be. If they did not want the extent of the government’s spying disclosed, they would surely shut down the presses that are reporting on this information.
The New York Times article I read yesterday is a case in point. The New York Times is perhaps the nation’s leading Illuminati propaganda distributor. What is reported in The Times is picked up and repeated by hundreds of other newspapers, periodicals, and various media distributors across the nation and the world.
What I suspect is happening, is the powers of the New World Order are seeking to condition the populace to the idea that being spied upon by the government is normal, necessary, and will not go away. Readers are left with a sense of powerlessness. Protest and you will be branded a terrorist or spy. Accept the government’s intrusive spying and you will be left alone.
Perhaps that is the distinction between Edward Snowden and James Risen and Nick Wingfield, the authors of the news article published by The New York Times. Risen and Wingfield, although disclosing far more damning information about the government’s collusion with technology companies, are reporting the information without protest. Their attitude is one of impartiality, or perhaps indifference. They merely report on the current state of things, but they do not raise any alarm about loss of privacy, or the dramatic expansion of government intrusion into the lives of its citizens. The following excerpts from The New York Times article disclose the interconnectedness of government spying agencies and technology companies.
To get their hands on the latest software technology to manipulate and take advantage of large volumes of data, United States intelligence agencies invest in Silicon Valley start-ups, award classified contracts and recruit technology experts…
Despite the companies’ assertions that they cooperate with the agency only when legally compelled, current and former industry officials say the companies sometimes secretly put together teams of in-house experts to find ways to cooperate more completely with the N.S.A. and to make their customers’ information more accessible to the agency… They are also under subtle but powerful pressure from the N.S.A. to make access easier.
Skype, the Internet-based calling service, began its own secret program, Project Chess, to explore the legal and technical issues in making Skype calls readily available to intelligence agencies and law enforcement officials, according to people briefed on the program who asked not to be named to avoid trouble with the intelligence agencies.
Project Chess, which has never been previously disclosed, was small, limited to fewer than a dozen people inside Skype, and was developed as the company had sometimes contentious talks with the government over legal issues, said one of the people briefed on the project. The project began about five years ago…
A Skype executive denied last year in a blog post that recent changes in the way Skype operated were made at the behest of Microsoft to make snooping easier for law enforcement…
Microsoft executives are no longer willing to affirm statements, made by Skype several years ago, that Skype calls could not be wiretapped…
Many software technology firms involved in data analytics are open about their connections to intelligence agencies. Gary King, a co-founder and chief scientist at Crimson Hexagon, a start-up in Boston, said in an interview that he had given talks at C.I.A. headquarters in Langley, Va., about his company’s social media analytics tools.
The future holds the prospect of ever greater cooperation between Silicon Valley and the N.S.A…
[Source: http://www.nytimes.com/2013/06/20/technology/silicon-valley-and-spy-agency-bound-by-strengthening-web.html]
Visit the following link and you will get an idea about the scope of the attention The New York Times is giving to this subject. Day after day the populace is being bombarded with articles on government spying. All this attention seems intent on bringing the subject out in the open while controlling the conversation to make it seem reasonable for the government to gather vast amounts of data on its own citizens.
http://topics.nytimes.com/top/reference/timestopics/organizations/n/national_security_agency/index.html
Mainstream media is downplaying any government overreach, and is emphasizing a message that spying on citizens, and gathering vast reams of data on them, is not a cause for concern. This bias is revealed in the heading of the following news article.
Why Surveillance Draws Little Outcry
June 11, 2013By Ben Werschkul, Pedro Rafael Rosado, Alyssa Kim and Marcus Mabry
[Source: http://www.nytimes.com/video/2013/06/11/us/100000002275350/why-surveillance-draws-little-outcry.html]
Is there truly no outcry over the government’s surveillance programs, or is The New York Times attempting to make it appear so? I am convinced that it is the latter. Those raising an alarm are denied a voice in the mainstream media to express their concerns. This is how the powers that be shape public opinion. They marginalize the dissenters, criminalize the whistleblowers, and emphasize the fairy tale view that everything is business as usual, no cause for alarm.
Following are some excerpts from another news article that I came across yesterday after I posted the blog on Big Brother.
Is the Government Spying On You Through Your Own Computer’s Webcam Or Microphone?
June 24, 2013
Source: Washington’s Blog
Government – Or Private Individuals – May Be Watching and Listening
We documented earlier today that – if you are near your smart phone – the NSA or private parties could remotely activate your microphone and camera and spy on you.
This post shows that the same is true for our computer.
Initially, the NSA built backdoors into the world’s most popular software program – Microsoft Windows – by 1999.
And a government expert told the Washington Post that the government “quite literally can watch your ideas form as you type” (confirmed).
Reuters documented last year that the U.S. and Israeli governments can remotely turn on a computer’s microphone:
“Evidence suggest that the virus, dubbed Flame, may have been built on behalf of the same nation or nations that commissioned the Stuxnet worm that attacked Iran’s nuclear program in 2010 [i.e. the U.S. and Israel], according to Kaspersky Lab, the Russian cyber security software maker that took credit for discovering the infections.
Kaspersky researchers said they have yet to determine whether Flame had a specific mission like Stuxnet, and declined to say who they think built it.
Cyber security experts said the discovery publicly demonstrates what experts privy to classified information have long known: that nations have been using pieces of malicious computer code as weapons to promote their security interests for several years..
Flame can gather data files, remotely change settings on computers, turn on PC microphones to record conversations, take screen shots and log instant messaging chats.
Kaspersky Lab said Flame and Stuxnet appear to infect machines by exploiting the same flaw in the Windows operating system and that both viruses employ a similar way of spreading…
PC Magazine tech columnist John Dvorak writes:
From what we know, the NSA has back door access into Apple, Microsoft , and Google…
Microsoft is the source of the operating system for Windows and Windows cell phones. Apple controls the OS for Macs, iPhones, and iPads. Google controls the Chrome OS, Chrome Browser, and Android cell phones. The companies regularly push operating system upgrades and security updates to users on a regular basis.
Imagine however that the NSA has access to these updates at the source and has the ability to alter these updates in order to install some sort of spyware on your phone, tablet, or computer. The software could turn on your camera or microphone remotely, read all your private data, or erase everything and brick your phone or computer.
Moreover – as documented by Microsoft, Ars Technica, cnet, the Register, Sydney Morning Herald, and many other sources – private parties can turn on your computer’s microphone and camera as well.
Cracked noted in 2010:
All sorts of programs are available to let you remotely commandeer a webcam, and many of them are free. Simple versions will just take photos or videos when they detect movement, but more complex software will send you an e-mail when the computer you’ve installed the program on is in use, so you can immediately login and control the webcam without the hassle of having to stare at an empty room until the person you’re stalking shows up.
The bottom line is that – as with your phone, OnStar type system or other car microphone, Xbox, and other digital recording devices – you shouldn’t say or do anything near your computer that you don’t want shared with the world.
Postscript: You could obviously try to cover your webcam and microphone when you don’t want to use them.
[Source: http://www.blacklistednews.com/Is_the_Government_Spying_On_You_Through_Your_Own_Computer%E2%80%99s_Webcam_Or_Microphone%3F/26892/0/0/0/Y/M.html]
My purpose in sharing this information is NOT to incite protest, nor to cause alarm. Rather, it is to inform the people of God of the true state of things that they might walk wisely in the midst of a crooked and perverse generation.
It is quite reasonable to conclude that the mega corporations that dominate all areas of communications technology have been working in collusion with government spy agencies for a long time. If any company proved unwilling to cooperate with the government, there were ways to apply pressure upon them. The same powers that run the government also control banking and the media. Simply cut off a company’s access to financing, or begin a media smear campaign to cause a company to lose favor with the public. If all else fails, a hostile corporate take-over can always be arranged whereby a company that is complicit with the government can take ownership of some less compliant technology company, and bring it into line with the government’s wishes. This is evidently what occurred when Microsoft acquired Skype in 2011.
Shortly after Microsoft purchased Skype, fundamental changes were made in the way Skype routes its communications sessions. Following is an excerpt from an Internet source:
According to CNN, hackers and bloggers are saying the changes, which push some of the video calling process onto Skype’s own computers instead of onto random machines on the Internet, could help the app spy on users’ calls, presumably at the request of a court or government.
“Reportedly, Microsoft is re-engineering these supernodes to make it easier for law enforcement to monitor calls by allowing the supernodes to not only make the introduction but to actually route the voice data of the calls as well,” Tim Verry, from the website ExtremeTech, wrote last week. (Supernodes are third-party computers that act as a sort of directory service for routing calls.)
“In this way, the actual voice data would pass through the monitored servers and the call is no longer secure. It is essentially a man-in-the-middle attack, and it is made all the easier because Microsoft — who owns Skype and knows the keys used for the service’s encryption — is helping.”
[Source: http://lissnup.wordpress.com/2012/07/27/skype-whos-listening/]
It would be well that the saints today take the words of King Solomon to heart.
Ecclesiastes 10:20
Furthermore, in your bedchamber do not curse a king, and in your sleeping rooms do not curse a rich man, for a bird of the heavens will carry the sound, and the winged creature will make the matter known.
Did you ever wonder where the saying, “A little bird told me” originated? Solomon is to be credited with it.
Modern technology has breathed new life into this old proverb. Therefore, be careful what you tweet!
May you be blessed with peace and understanding in these days.
NSA Logo Parody
NSA: National Security Agency
NSA Alternate Acronym: Nothing Secure Anymore
I am not an anarchist, nor am I a rebel. I do not advocate armed resistance against the governments of the world, nor am I a proponent of political activism. Although I often write posts on the actions of the governments of the world, particularly of my home nation the United States, my purpose in doing so has nothing to do with inciting people to engage in actions against the government. Aside from such efforts being vain (for nothing in the political realm is as it seems on the surface), the Christian should see himself as an alien and a stranger in this world, avoiding becoming entangled with worldly affairs which distract from the labors of the kingdom of God.
II Timothy 2:3-4
Suffer hardship with me, as a good soldier of Christ Yahshua. No soldier in active service entangles himself in the affairs of everyday life, so that he may please the one who enlisted him as a soldier.
II Corinthians 10:3-5
For though we walk in the flesh, we do not war according to the flesh, for the weapons of our warfare are not of the flesh, but divinely powerful for the destruction of fortresses. We are destroying speculations and every lofty thing raised up against the knowledge of God, and we are taking every thought captive to the obedience of Christ…
John 18:36
Yahshua answered, “My kingdom is not of this world. If My kingdom were of this world, then My servants would be fighting, that I might not be delivered up to the Jews; but as it is, My kingdom is not of this realm.”
My purpose in writing on the affairs and actions of governments is to promote wisdom and understanding among the people of God. It is to peel away layers of deception that the saints in Christ might walk wisely, with their eyes opened to the reality of the world in which they live. The Son of God spoke the following words to His disciples.
Matthew 10:16-17
“Behold, I send you out as sheep in the midst of wolves; therefore be shrewd as serpents, and innocent as doves. Beware of men…”
There is no virtue in ignorance. Indeed being misinformed, or deluded regarding the state of this world, can result in much harm to the people of God. The world around us is a very deceptive place. Many Christians are living in a land of illusion, oblivious to the true nature of this dark and evil world. This post is offered to make the reader aware of some developments in the societies in which we live which will undoubtedly affect them going forward.
I have noted a number of new products being released recently that serve a purpose which is hidden from the consumer. These are spy products. They give the government a means to enter into people’s homes, observe all that is done, record every word, giving the global masters insight into the very thoughts which are in an individual’s mind. One remarkable product marketed by Amazon, the world’s largest internet retailer, is Echo. To understand the capabilities of Echo, I am providing the following video. (No longer available)
Twenty seconds into the video, the young girl and her father have the following conversation.
Daughter: “Is it on?”
Father: “It is always on.”
Daughter: “Can it hear me right now?”
Father: “No. It only hears you when you use the wake word we chose. Alexa.”
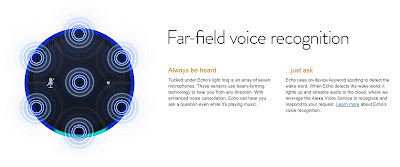
When the wife speaks in an overly loud voice to the device, the husband says, “You don’t actually have to yell at it. It uses far-field technology so it can hear you from anywhere in the room.”
Far Field Voice Technology
Always be heard
Tucked under Echo’s light ring is an array of seven microphones. These sensors use beam-forming technology to hear you from any direction. With enhanced noise cancellation, Echo can hear you ask a question even while it’s playing music.
The dialogue of the Amazon video is disingenuous. When the daughter asks her father, “Can it hear me now,” the answer she receives is not technically correct. In order for Echo/Alexa to know when its wake word has been spoken, it has to be listening all the time. Echo responds only after its wake word has been heard, but it is listening constantly. Since Echo requires a constant internet connection to operate, it is able to transmit what it hears continuously.
With the far-field voice technology, likely developed by DARPA, Echo is able to eavesdrop on every word spoken by every person within its range of hearing. For those unfamiliar with the term, DARPA is the U.S. Defense Department’s research arm. It is tasked with developing a wide range of technologies the government may use for both military and non-military purposes, including spying on its citizens. It is not mere speculation that the technology used in Echo has come from the Defense Department. When Apple released its intelligent assistant for the iPhone, known as SIRI, it was revealed that the technology came from DARPA.
Don’t let her dulcet voice and easygoing, eager-to-please manner fool you. Behind Siri, the voice-controlled personal assistant app destined to power Apple’s iPhone 4S, lies the heart of a hardened combat veteran. That’s because the technology was spun out of the Defense Advanced Research Projects Agency (DARPA), the Pentagon’s high-tech research and development arm.
While Siri was developed as cognitive software with artificial intelligence baked into its code—designed to learn from experience and respond to ever-changing threats on the battle field – iPhone users will find more prosaic uses for it as a hands-free replacement for the touch screen…
Over the last half century, DARPA technology has led to predator drones, night vision goggles, GPS, and even the Internet. It’s invested heavily in telesurgery, exoskeletons that function like wearable robots, landmine detection (including one technique that relies on honeybees), a flying car, handheld speech translation, and biosensors, as well the usual deadly array of guns, bombs, stealth planes and missiles.
[Source: http://www.fastcompany.com/1785221/siri-ously-darpa]
The same people who developed the Predator and Reaper Drones capable of firing missiles at human targets, developed the technology behind SIRI and Echo. There is a unified purpose between both the deadly drones and these computer technologies. It is to monitor, identify, and eliminate threats. One can easily envision the technologies being used together. Did you note that DARPA also developed the technology that led to the Internet? The Internet serves a fundamental and irreplaceable function for the masters of the military-industrial complex. It is a treasure trove of data, revealing a wide array of information about the people, companies, and organizations who use it.
Hollywood has given us hints of what the powers-that-be are up to. In the movie Captain America – The Winter Soldier it is revealed that the government is identifying human targets that pose a threat to their power. The plan is to eliminate these threats BEFORE they commit a crime, or some actionable offense against the government. The Internet has been used to gather information on all people, and a special algorithm has been developed to analyze the information to identify threats.
“Zola’s algorithm is a program for choosing Insight’s targets,” Sitwell spit out…
“What kind of targets”? Cap asked.
“You!” Sitwell yelled, waving his hand, “A T.V. anchor in Cairo, the Under-Secretary of Defense, a high-school valedictorian in Iowa City…, anyone who’s a threat to Hydra. Now, or in the future…”
Cap glanced at me, his forehead creasing, “How could it know?”
“How could it not? The 21st century is a digital book! Zola taught Hydra how to read it. Your bank records, medical histories, voting patterns, e-mails, phone calls, your… SAT scores! Zola’s algorithm evaluates people’s past to predict their future.”
“And what then?” Natasha tried to clarify…
“What then!” Cap repeated forcefully.
“The the Insight helicarriers scratch people off the list,” Sitwell spit, “a few million at a time.”
Added to the list of data sources one could mention “your private conversations,” for the government has been monitoring them for years. Cell phones are one of the chief sources for this monitoring, for people tend to carry them everywhere they go. The government is able to activate the microphone in a cell phone at any time, and listen in, even when the individual is not making a call. I have mentioned this capability in the past, as well as other means by which the government spies on the public.
A Word to the Wise – Big Brother is Watching You
https://parables.blog/2013/06/a-word-to-wise-big-brother-is-watching.html
A Little Birdie Told Me
https://parables.blog/2013/06/a-little-birdie-told-me.html
What the government is aiming for is a total surveillance state. They do not want there to ever be a time when people are not being monitored, their location and actions unknown. Products like Amazon Echo are advancing this total surveillance state, giving the government entrance to places people once thought was their private sanctuary (and many still do). Amazon Echo is a fantastic product. It offers a wealth of functionality for a small price. I myself would like to have many of the features that it makes available. It would be nice to say a word and play a song, start a timer, or add an item to my grocery shopping list. These “smart” capabilities come at a price, however. The price is a loss of privacy, for every word spoken in range of the Amazon Echo will be monitored.
The government and media are always playing deceptive games with people. They disclose some NSA spying program, suggesting that the government is collecting “meta-data,” but not recording actual conversations. You can be assured this is not the truth. The disclosures of government capabilities are usually twenty years old, with the current state of technology never being disclosed. In this way they shape the thoughts of the populace, steering them away from the enormous scope and capabilities of the government’s spying apparatus today.
Don’t plan to purchase the Amazon Echo? How about upgrading to Windows 10? It will turn every desktop computer, laptop, tablet, and phone that it is installed on into something far more capable than Amazon Echo. Instead of Alexa, there will be Cortana. The software will use the computer’s camera to perform facial recognition and iris scanning to know precisely who is sitting in front of the computer screen. The microphone will be always on so that it can be voice operated as a person speaks the wake word “Cortana.”
“Let me tell Cortana more things about me so I can have more of that proactive interaction.”
Who are you really talking to when you share all these personal things about yourself? NSA? CIA? FEMA? DHS? FBI? The answer is, “All of the above!”
Cortana
The EYE is watching YOU!
The Windows 10 software and its capabilities are awesome. They include many features that computer users would want. It was reported by the Seattle Times that Microsoft spent $10 billion dollars developing Windows Vista which was released in 2005. 10,000 employees worked for five years developing that iteration of their operating system. Forbes reported that Microsoft would spend $1.5 to $1.8 billion just on marketing for Windows 8 when it was released in 2012. How many billions of dollars did Microsoft spend to develop Windows 10, only to offer it as a free upgrade to virtually anyone who has a computer capable of running it? I have not seen the figures, but it must be an enormous amount.
This begs the question “Why?” Why are companies like Microsoft and Amazon investing so much in these technologies and selling them so cheaply? If you understand the nature of the global corporate governmental cabal, you already know the answer. The powers-that-be control both the corporations and the government. They are pursuing the same goals. DARPA gives the technology to corporations like Apple, Amazon, Microsoft and others who implement the technology for the government. The government passes along multi-billion dollar contracts to these corporations, insuring that they don’t lose money.
A few years back I read a news article that revealed that Jeff Bezos, the CEO of Amazon, was attending CFR meetings (Council on Foreign Relations). He has been listed as an attendee of the Bilderberg meetings. The list below is from the 2013 meeting, a time when both Amazon Echo and Windows 10 were in development. You will find among the Bilderberg attendees the name Craig J. Mundie. He is listed as “Senior Advisor to the CEO, Microsoft Corporation.” His responsibilities actually go far beyond this, for he is the Chief Research and Strategy Officer for Microsoft. Where do these men get their marching orders? From the global leaders at CFR, Bilderberg, and similar groups.
Note that Mr. Mundie is also listed as “a member of President Obama’s Council of Advisors on Science and Technology.” Equally disturbing, he has reportedly advocated that all individuals be licensed to use the Internet. Government and industry are working hand in hand.
Heart4God Website: http://www.heart4god.ws
Parables Blog: www.parablesblog.blogspot.com
Mailing Address:
Joseph Herrin
P.O. Box 804
Montezuma, GA 31063






















0 Comments